
Why is SkyBridge® Proxy DLL so safe?
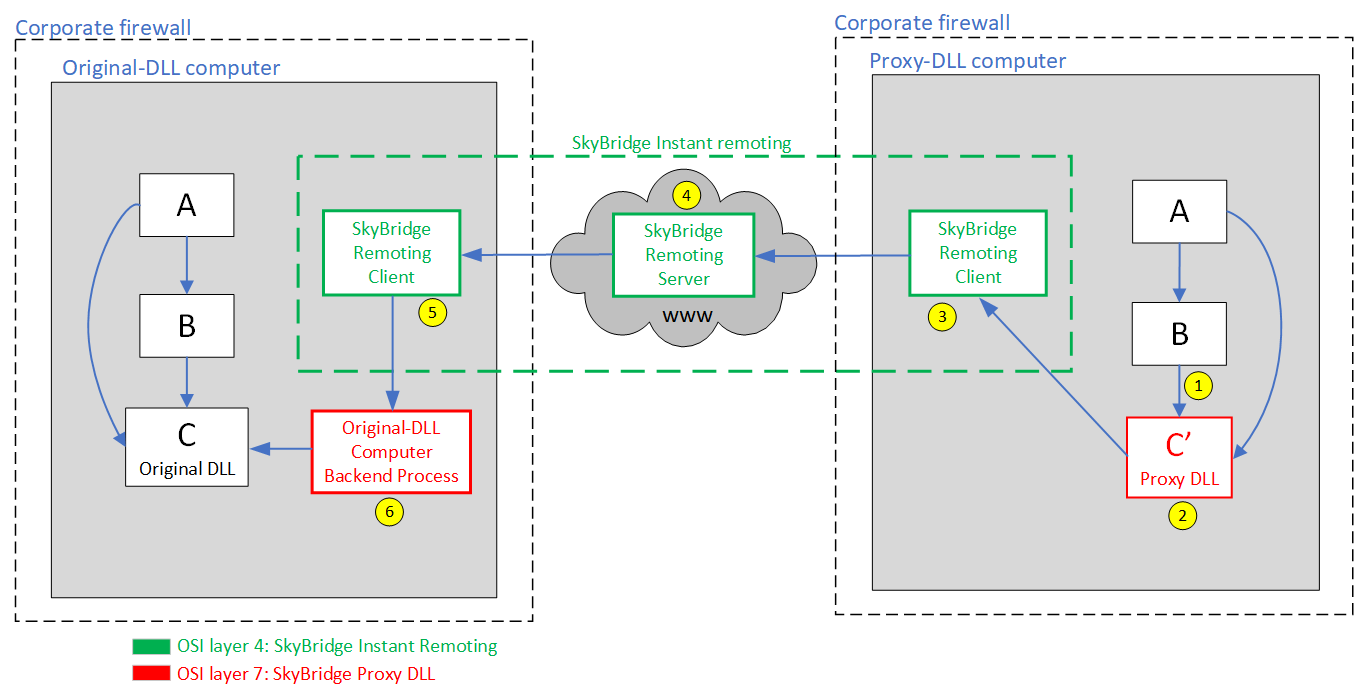
The round trip
Step 1
Some code calls a function on the proxy DLL.
Step 2
The called function serializes the invocation details (type of the class, function name, parameter values) into a JSON string and asks the SkyBridge® Instant Remoting layer to route it to the original DLL.
Step 3
The Instant Remoting client on the proxy-DLL computer establishes a TCP connection with the Instant Remoting server in the cloud.
The connection is encrypted using the same Transport Layer Security (TLS) protocol that is used by a browser to connect to a bank. Legacy TLS protocols are not accepted.
After the TLS handshake succeeds, the client sends the account ID and password to the server. The password is hashed using a computation-extensive hashing algorithm and compared with the hash stored in the database.
Then, the client breaks up the JSON string into many tiny packets and sends them one by one to the server.
Step 4
The SkyBridge® Instant Remoting servers are hosted in AWS and employs multiple layers of AWS defence measures.
As soon as the server receives a packet, it forwards it to the Instant Remoting client on the original-DLL computer, which maintains a secured TCP connection with the server. That client reassembles the packets into the JSON string.
The server never tries to interpret or log the payload of the packets. Moreover, it is impossible for the server to infer any meaning from the data shard in a single packet.
Step 5
The client on the original-DLL computer passes this JSON string to the SkyBridge® backend process.
Step 6
The backend process attempts to deserialize the JSON string into a call on one of the functions on the original DLL, then invokes that function with the parameter values contained in the JSON string, and returns the result (return type and "out" or "ref" parameter values) to the function on the proxy DLL that was initially called.
If it fails to deserialize the JSON into a call on a function on the original DLL, it throws an exception.
Therefore, SkyBridge® Proxy DLL is inherently safe
- Both the original-DLL computer and the proxy-DLL computer only has an outgoing TCP connection to connect to port 52888 on the SkyBridge® server.
- The proxy-DLL computer does not listen to any instruction coming from the outside world via the TCP connection.
- The backend process on the original-DLL computer does listen to instructions coming from the outside, however, even if a malicious party gains control of the proxy-DLL computer or the SkyBridge® server, there is nothing he can do to the original-DLL computer exception for calling one of the functions on the original DLL. Therefore, the original DLL is the sandbox that an attacker can never get out of.
More about the SkyBridge® Proxy DLL technology
To know more, watch demos, download the Proxy DLL binaries, sample projects and documentations, go here.